
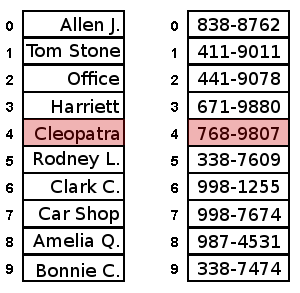
Hash tables are a tremendous tool for a computer scientist's toolbox because they allow for very quick information storage and retrieval. Hash tables make use of two regular lists: one to store the index data, or keys, and the other to store the data, or values. Each key is paired with its own value and entered at equal points in the two lists (see red highlighted region of image).
When someone wants to know Cleopatra's phone number, it is then possible to move through the list of keys until Cleopatra's name is discovered, then look up the phone number from the list of values with the equivalent index (if Cleopatra's name is stored in slot 4 of the key list, her phone number will be stored in slot 4 of the values list). In reality, it is not necessary to move through the list in order; there is a special technique called hashing (hence the name 'hash tables') that makes it possible to find elements in far less time. We won't go into the details of that technique here, but the combination of hashing with the two lists is what gives the hash table its power.
Feel free to check out the Wikipedia article on hash tables for more information.